Comprehensive Application & API Security
We deliver in-depth security testing across web apps, mobile platforms, APIs, and source code through a blend of manual, dynamic (DAST), static (SAST), and runtime analysis. From business logic flaws and injection risks to insecure APIs and cryptographic misuse, our experts uncover what automated scanners can’t. Aligned with OWASP, MASVS, and industry standards, we ensure security is embedded from architecture to code.
Our experts perform deep analysis of your web applications using manual, dynamic (DAST), and static (SAST) techniques to uncover real-world exploitable weaknesses.
✅ Key Focus Areas
- Injection Attacks – SQLi, Command Injection, Host Header Injection
- Cross-Site Scripting (XSS) – Reflected, Stored, and DOM-based
- Authentication & Session Management – Brute force, session fixation, token theft
- Business Logic Flaws – Logical bypasses, multi-step abuse
- Broken Access Control & IDOR – Unauthorized data access, privilege escalation
- File Upload Vulnerabilities – MIME spoofing, path traversal, upload-based RCE
- Client-Side Risks – DOM XSS, CSP misconfigurations, local token storage
- CSRF & SSRF – Exploiting weak trust boundaries
📏 Standards Followed
OWASP Top 10 • CWE/SANS Top 25 • OWASP ASVS • PCI-DSS / HIPAA (on demand)
📱 Mobile Application Security Testing
We secure Android and iOS mobile apps by performing static, dynamic, and runtime analysis across the app, OS, and network layers.
✅ Key Focus Areas
- Reverse Engineering & Binary Analysis – Decompiled code review, obfuscation checks
- Insecure Data Storage – Logs, cache, shared preferences, plist files
- Insecure Communication – TLS misconfigurations, MITM, SSL pinning validation
- Authentication & Token Management – Hardcoded credentials, token leakage
- Runtime Manipulation – Debug bypass, root/jailbreak detection bypass
- File Handling Vulnerabilities – World-readable files, sensitive backups, path traversal
- Insecure Inter-App Communication – Intent sniffing, exported components, broadcast abuse
- Backend API Integration Testing – Token abuse, BOLA, insecure endpoints
📏 Standards Followed
OWASP Mobile Top 10 • MASVS (L1/L2) • PCI-DSS / HIPAA (on request)
🧑💻 Source Code Review
We perform comprehensive manual and automated source code reviews to detect hidden, business-impacting vulnerabilities that scanners often miss. Our approach covers both secure coding and logic-based flaws.
✅ Key Focus Areas
- Input Validation Issues – Untrusted user inputs, missing sanitization
- Authentication Logic Flaws – Bypass, insecure token flows, broken logic
- Authorization Misconfigurations – Privilege escalation, role manipulation
- Sensitive Data Exposure – Hardcoded secrets, credentials, API keys, tokens
- Insecure Cryptographic Implementations – Weak hashing, hardcoded keys, misuse of crypto APIs
- Error Handling & Debug Code – Verbose errors, stack traces, debug endpoints
- Insecure File & Resource Access – Path traversal, file inclusion flaws
- Third-Party Dependencies – Outdated libraries, unsafe package usage
📏 Standards Followed
OWASP ASVS • OWASP Top 10 • SEI CERT • Custom secure coding guidelines
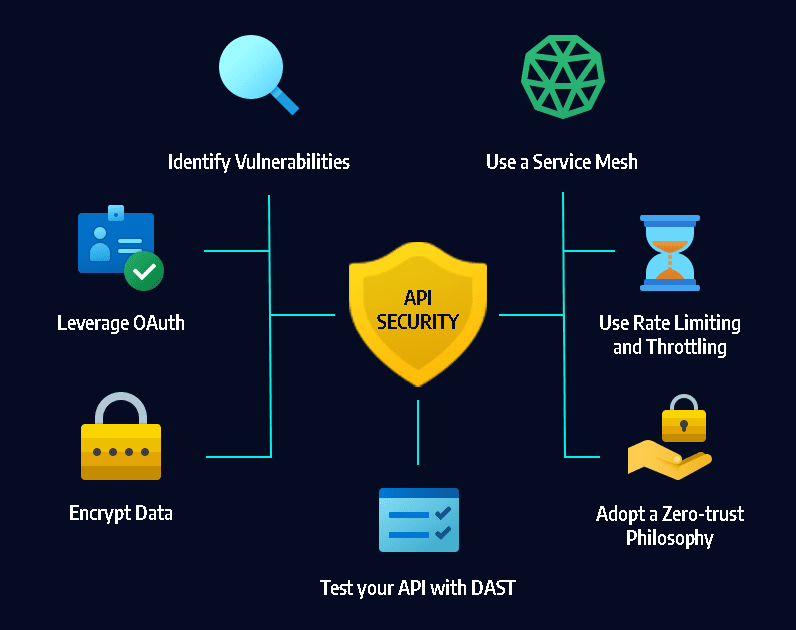
🔐 API Security Assessment
Our API testing methodology is built to uncover deep logic flaws and broken authorization models, which are often overlooked in traditional assessments. We test REST, GraphQL, WebSocket, and SOAP APIs.
✅ Key Focus Areas
- Broken Object-Level Authorization (BOLA) – IDORs in API endpoints
- Authentication & Token Security – JWT flaws, token replay, hardcoded keys
- Rate Limiting & Abuse Protection – Brute force, enumeration, abuse resistance
- Mass Assignment & Field Tampering – Hidden field injection, over-posting
- Improper Input Validation – Injection risks (SQL, NoSQL, command, LDAP)
- Insecure Error Handling – Verbose API messages, stack traces
- Swagger/OpenAPI Fuzz Testing – Schema abuse, missing auth checks
- Session & Replay Attack – Cookie/header token handling
📏 Standards Followed
OWASP API Top 10 • OWASP Web Security Testing Guide • Custom schema validations